Assessment & Compliance Tools For Every IT Professional.
Every Issue. Every Risk. Every Change. Everywhere..
VulScan
Network Vulnerability Management For The Rest Of Us.
VulScan is a stand-alone internal and external scanning solution that can be scheduled to run whenever you want, wherever you want, and produce alerts of discovered vulnerabilities. It consists of a web-based management portal and licenses to set up as many network scanners as you need at any site using our software and Hyper-V or VMWare.
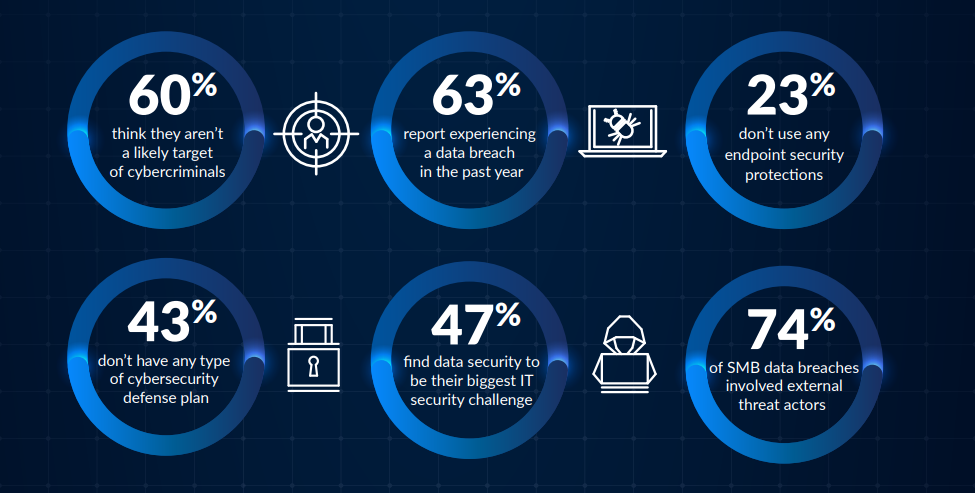
Small Businesses
ARE AT RISK
Hackers know the majority of smaller organizations are not prepared against network security breaches, making them popular targets for cyberattacks.
Vulernability Scan
FEATURES
Automate internal vulnerability scans to run at whatever schedule makes sense based on your maturity model. Get alerts with summary info upon scan completion. Access results in web portal to drill in and take action.
Automate internal vulnerability scans to run at whatever schedule makes sense based on your maturity model. Get alerts with summary info upon scan completion. Access results in web portal to drill in and take action.
A virtual appliance performs automated, scheduled scans of the systems on a network behind the firewall. Scans can be customized to specific IP addresses or address ranges
A virtual appliance is installed on a system outside the firewall which can be programmed to scan different public-facing IP addresses, typically a firewall of a computer network or a web or other public facing server.
Multiple scanners can be used to perform internal vulnerability scanning of a network, with the results of the scans combined into a single "site" for overall management of the systems in the network. Multiple scanners may be deployed within a single building/network or can be deployed to different locations/offices. Multiple scanners for a site only consume a single license.
Notification of scan results are automatically emailed to the technician. These results can be filtered by IP range or by severity
VulScan can automatically create tickets for discovered issues/vulnerabilities. The results can be filtered by IP range or by severity
Vulnerabilities can be marked as false positives or excluded to remove them from the dashboard and from future notifications. Multiple criteria can be set, including start and end dates, for greater flexibility when suppressing issues.
A Vulscan license to create a portable vulnerability scanner that can be used to perform one-off scans. Use cases include prospecting and project work
Quickly and easily generate reports that provide information on the vulnerabilities discovered that can be filtered using criteria like CVSS score and scan date range. The reports can be customized with your logo and colors.
Singe dashboard view that displays all organizations being managed with drill down to manage the individual site or sites contained within that organization.
Custom Scan Profiles allow you to customize your VulScan tasks. Specifically, you can create scan profiles to target specific TCP and/or UDP ports
Using credentialed/authenticated scans allows VulScan to access an account on a network endpoint - this can be a computer system or network device via SNMP.
BENEFITS
MSPs can create and deliver recurring internal vulnerability management services. Internal IT departments can insure that all network locations are being continuously scanned and managed to reduce risk.
MSPs can create and deliver recurring external vulnerability management services. Internal IT departments can insure that all network locations are being continuously scanned and managed to reduce risk.
Scans are performed on a regular basis to save the technician time. They are also only performed on the desired IP addresses to save scan time, or to avoid scanning specific systems (eg - printer).
Identifies issues on public facing systems for remediation to prevent hackers from gaining access through a firewall.
Using multiple scanners on a large network speeds up the scanning process, and allows disparate locations to be scanned and managed as a single site.
The technician only receives desired alerts, and saves the technician time by not having to login to the dashboard to retrieve results.
Saves time and ensures remediation is tracked in PSA system.
Reduces "noise" so that only important and desired vulnerabilities are presented in the dashboard, reports and notifications
Enables temporary internal vulnerability scanning of a network without having to perform an installation of a virtual appliance on a network, and does not consume a base license of the product. Easily support multiple locations with a single device
Reports can be provided to management to show results of the vulnerability issues and effectiveness of vulnerability management
Easily and effectively manage multiple organizations and sites
Allows you to perform low impact scans that address only those ports with which you are concerned to speed up scan durations and/or avoid scanning specific IPs/systems.
Enables a more thorough internal vulnerability scan which can help detect a wider range of security issues.
PERSONAL DATA
Small companies collect data, such as medical records, credit card information, social security numbers, bank account credentials or proprietary business information, that is easy to offload for a profit on the dark web.
ACCESS A LARGER TARGET
This is what happened in the Target breach, which resulted in 40 million stolen credit and debit cards. Hackers accessed the retail giant’s system through a third-party subcontractor that provided refrigeration and HVAC systems.
COMPUTING POWER
Cybercriminals can attack businesses through company computers and IoT devices and recruit them into an army of bots to perform massive DDoS attacks..
COLD HARD CASH
Money is a powerful motive, which is why ransomware is a popular method of attack. The average cost of a ransomware attack on a business is $133,000.