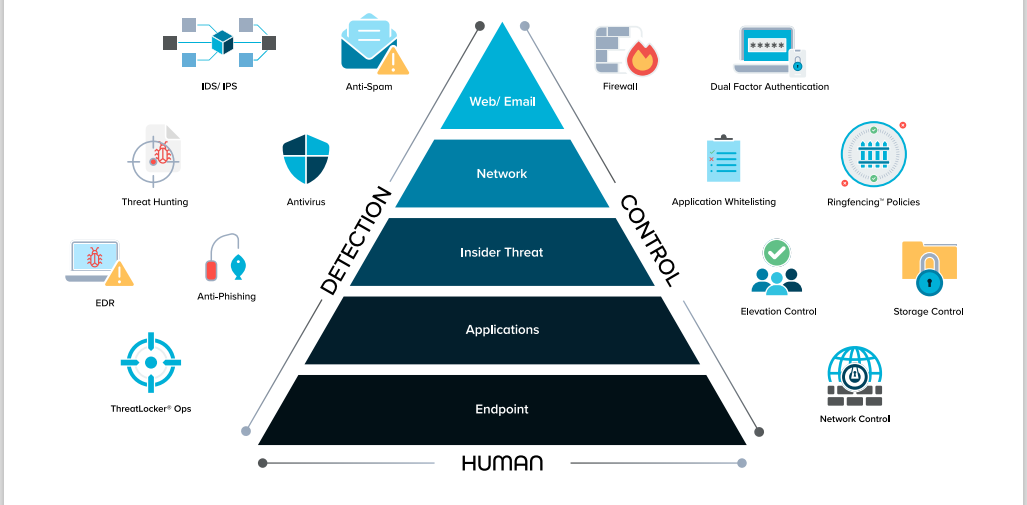
On the right side of the security triangle sit the control tools. These are the Zero Trust tools that provide proactive protection. Based on the rules you set, tools on this side of the triangle stop unwanted behavior instead of relying on machine intelligence to recognize and react to it. Firewalls control access to your network. Application Allowlisting dictates which applications can run in your environment. Ringfencing™ restricts what those permitted applications can access and interact with once they are running. Privileged access management (PAM) regulates the use of admin privileges. While proactive control tools provide effective protection, a robust cybersecurity approach will never solely rely on controls from a single side of the security triangle.
Take Control
When selecting the ThreatLocker® Endpoint Protection Platform to cover the control side of the triangle, you’re choosing a powerful front line of defense. Administered correctly, ThreatLocker® stops known and unknown threats, taking care of the heavy lifting. This leaves the tools on the detection and human sides of the triangle to serve as a backup defense. ThreatLocker® pairs well with the built-in Windows antivirus, subscription antiviruses, NextGen AVs, or EDRs/ XDRs/MDRs. Select your desired detection product based on your organization’s needs and budget. This detection technology won’t see much action with ThreatLocker® at the forefront of your defense. By implementing the ThreatLocker® Endpoint Protection Platform for control, a detection tool to serve as backup, and security training to help prevent human errors, you can provide first-class protection for your organization’s environment.


